What is Cyber Security?
Definition of Cyber Security
Cyber security (also known as cybersecurity) is a discipline of IT security that has become increasingly important in recent years, both internally and regarding the public.
It deals with protection against all kinds of risks and threats from cyberspace. The focus is on all elements of communication and information technology that are connected to the intranet or internet via corresponding online components and are therefore vulnerable per se. In terms of IT systems, cyber security primarily considers their technical components (communication components, applications, processed data and information), but also the processes whose work steps affect online components.
Cyber security relevance
The rise in relevant incidents year after year shows what is in store for businesses and individuals in an increasingly connected world. The pandemic years of 2020 and 2021, in which distributed working has led to a multiplication of potential points of attack between companies, private households with home or mobile office workplaces, and the communication links in between, foreshadows interesting statistical material. But the fact remains: In the complexity and dynamics of modern infrastructures, especially with regard to Industry 4.0 and IoT, this becomes an undertaking that, if it goes awry, can quickly attack the economic viability of the company.
In the clinical or infrastructure environment, critical incidents can actually endanger life and limb. For this reason, governments define special requirements for these critical infrastructures, exemplified by CRITIS in Germany, the ISO 27000 journey and the BSI 200 standards.
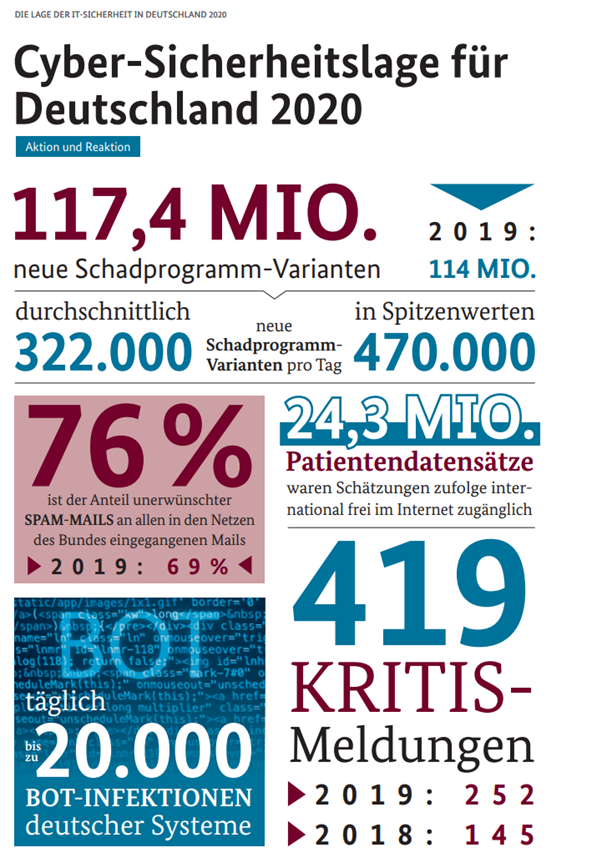
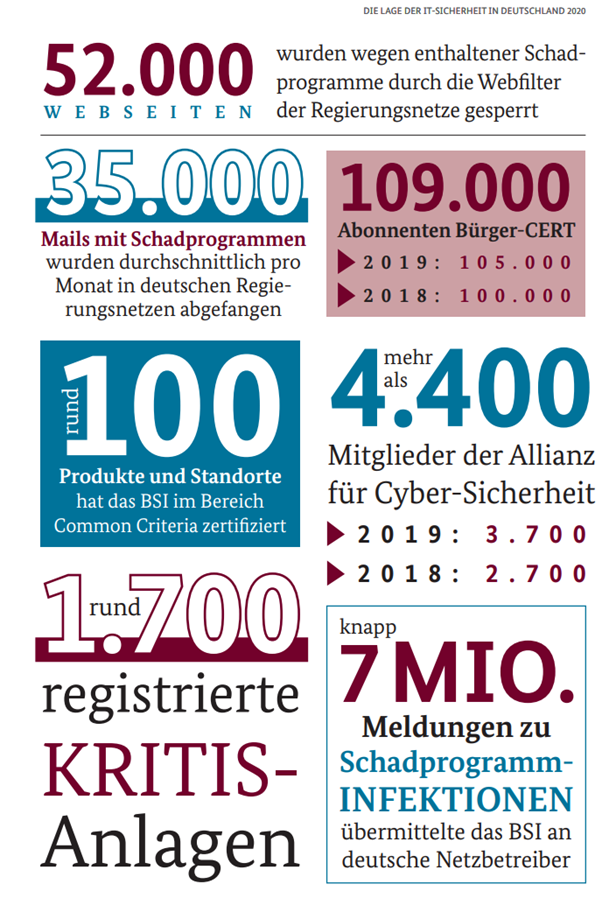
Figure 1: IT security in Germany 2020
Source: BSI-LB20/509: Die Lage der IT-Sicherheit in Deutschland 2020, Bundesamt für Sicherheit in der Informationstechnik (BSI), S. 36/37
Cyber threats as a challenge for organizations and companies: Cyber security is more than virus protection and DMZ
The discipline of cyber security is characterized by complexity and dynamism. It combines aspects from a wide variety of perspectives, but also has interfaces and overlaps with other disciplines.
The need for cyber security is no longer science fiction, but hard reality: whether it is an unintentional or targeted virus attack, internally or externally driven data theft, ransomware attacks on end devices as well as central systems for the purpose of blackmail, or simply trials of strength with scripts -Kiddies, experience-oriented zero-day exploitists through to real hackers with specific assignments from the broad field of economic and industrial espionage, or pure destructiveness and the desire for chaos and/or attention: cyber security deals with all of these scenarios .
Our reading and subscription tip: the BSI’s annual report “The situation of IT security in Germany” is published annually and is available free of charge online and as a print edition.
An absolute must-read for anyone interested in the subject.
Cyber threats as a challenge for organizations and companies
Cyber security is largely to be understood as risk management. Whether financially oriented cybercrime (e.g. in the form of the increasing number of phishing and ransomware attacks, including subsequent attempts at blackmail), politically motivated cyberattacks (e.g. to disclose genuine or disseminate falsified critical information to discredit public officials), or genuine cyberterrorism (e.g. attacks on control units of critical infrastructure elements) to create widespread chaos, panic and instability:
In the context of cyber security, it is always necessary to foresee new and ever more innovative attack variants, to harden infrastructures and organizations and to react appropriately to experienced digital attack situations.
On the attacker side, there are always completely new “professions” for which cyber security has to prepare. A few years ago, many of the current threats were only theoretically conceivable, but could hardly be implemented in practice.
With the increasing networking of all areas of life in the different economic sectors, it is apparently more and more “worthwhile” for criminal elements of different weight classes and different target orientations to become active. Especially in the context of Industry 4.0 and the Internet of Things (IOT), completely new threat scenarios are emerging: the more components of daily life have direct contact with the Internet, the greater the potential for damage and the associated attractiveness for disruptors.
On the side of those affected, there are not only “small, overwhelmed medium-sized companies” who do not have sufficient resources and skills to protect themselves effectively or at least to be able to react appropriately. Large companies and increasingly also state organizations, which at least theoretically have legions of capable architects, hardware and software experts at their disposal, are struggling with the situation. In some cases, the potential image damage is much higher than the direct economic damage caused by data loss or corrupt data, for example.
Goals of cyber security - not just processes and measures, but (also) a state
Very similar to how information security describes both processes and a state, cyber security also has a defined target image: the state of a security situation in cyberspace in which risks from this for one’s own organization are reduced to at least an appropriate level.
There is no such thing as absolute security, especially not in cyberspace. Even if a lot of hope is placed, for example, in future support from artificial intelligence, with the dynamics and complexity of the virtual world, the almost infinite number of interfaces and the bringing together of potentially very different interests worldwide:
On a permanent virtual construction site, where every little screw can represent a potential weak point, perfect risk prevention is simply not possible by human standards. It will always be a game of cat and mouse.
The aim must therefore be that in a management system, points of attack and risks with the probability of occurrence and potential damage are clearly analyzed, evaluated and ideally neutralized in advance using suitable means.
And on the other hand, on the measures side, if a cyber security incident occurs, the effects are reduced as far as possible – through clear responsibilities, unambiguous process, and information channels as well as dynamically adaptable or even self-regulating emergency plans.
framework of cyber security
Cyber security as a discipline is critical, but there is discussion about where its limits are and what requirements must be met.
On closer inspection, there are hardly any detailed guidelines on cyber security, which is of course also due to the dynamic nature of the topic. Many specifications are generally and technology-independently defined in the form of guiding principles or basic rules and can therefore be adapted relatively easily to new developments.
The requirements, which are formulated, can be found within the company in explicit or implicit company descriptions and procedural instructions, rules of conduct and the like.
There are also legal requirements and specifications, in Germany for example
- in the IT-SiG
- by the BSI
- in the KRITIS specifications
- in the GDPR
- in the ISO/IEC-27000 series
- with increasing relevance in IEC 62443 in the industrial environment
Cyber Security Benefits and Issues: Security vs. Productivity
IT, in its self-image as an enabler of modern corporate strategies, must also be aware of the simultaneous role as a security risk. As much as the requirements and models of cyber security can be adapted to new realities, and as good as the target image of a stable security situation is (or seems) achieved in a moment, it is still a snapshot of a dynamic situation:
In addition to technological leaps and increasingly creative attack tools from the other side, every new or changed infrastructure element (process step, hardware component, software update, configuration change, employee, or service provider, …) also harbors the potential for a security risk internally, which, strictly speaking, must be checked for itself and in the overall operational context.
However, the much-cited “Security by Design” approach, which propagates the holistic consideration of security aspects from the very first moment of planning, often falls by the wayside in favor of an operative efficiency target – especially in the case of components that are not directly obviously critical.
Above all, large companies with complex processes and architectures find themselves in a quandary again: They are almost forced to restrict themselves and their employees in dealing with IT, going far beyond authorization concepts, software guidelines and BYOD regulations. The central desire for a stable and long-lasting technical basis, reduced proliferation and lower, i.e., better manageable, complexity is absolutely understandable.
In doing so, they slow down organizational and IT-technical work processes in day-to-day operations, so to speak, with the announcement, felt or real.
The role of (IT) management in the highly dynamic field of tension between risk tolerance and work efficiency in day-to-day operations is not enviable, especially since many tools are found at levels other than the technical IT level and are therefore not easy to automate.
Future trends and challenges of cyber security
Cyber security is the constant struggle at the border between organizations and cybercriminals or cyberterrorist attackers. It is a matter of constant arming on both sides, both at the state level in the fight against criminally induced cyberterrorism or other states, at the private sector level with industrial and economic espionage, or at the personal level in the protection of private data or against concrete risks to life and limb Life, for example against the background of emerging autonomous driving on public roads.
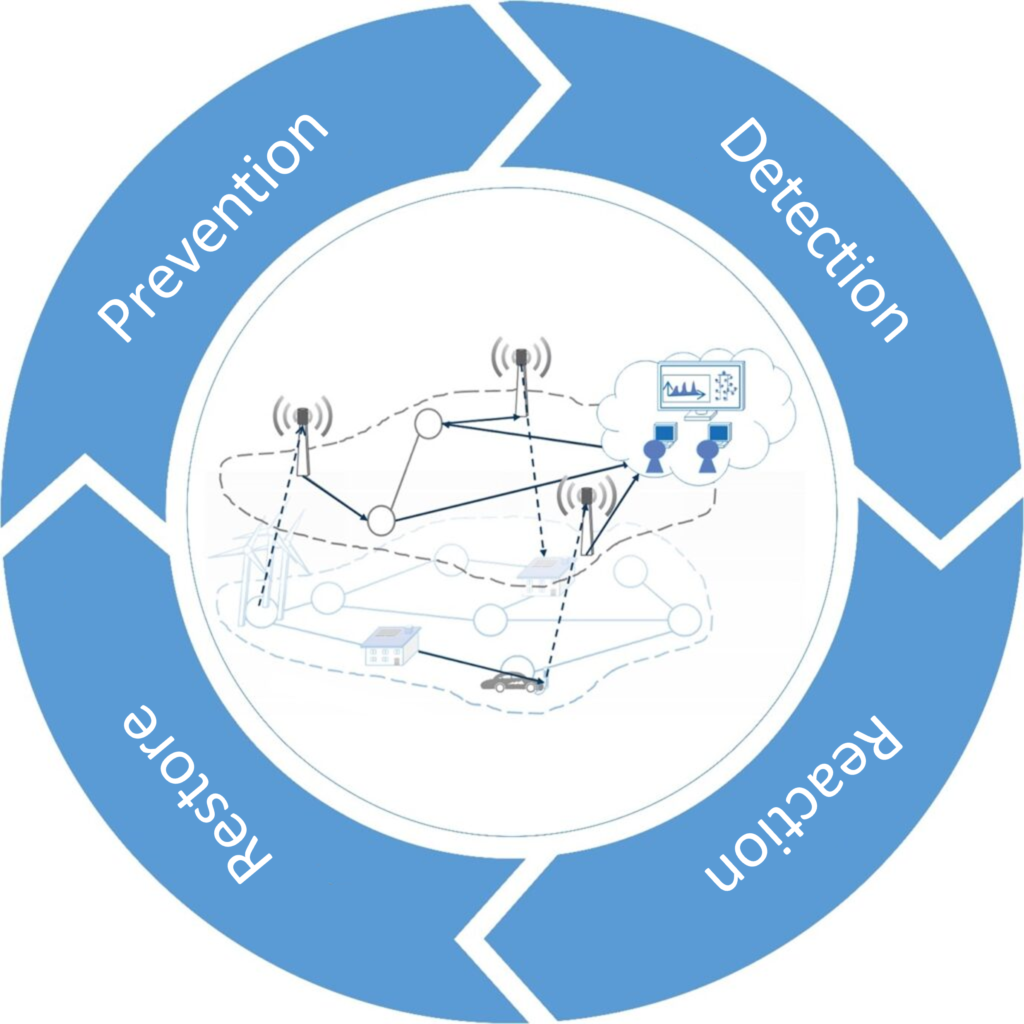
Figure 2: Cyber security is the constant struggle at the border between organizations and cybercriminals or cyberterrorist attackers
Source: https://www.iaew.rwth-aachen.de/cms/IAEW/Wirtschaft/Energiesystemstudien/Digitalisierung/~jalau/Cyber-Security/
What happens when arms competition leads to leaps in technology? When previously secure communication protocols between individual technical components are severely compromised? When individual attackers become cloud-based attacker cohorts that are controlled decentral or act completely autonomously and put infrastructures at different weak points under stress? When artificial intelligence finally appears on the field, which independently checks attack scenarios for known vulnerabilities – or even worse: starts to think about them independently?
Assuming that the social and economic framework conditions remain largely stable and that the interests of cybercriminal elements do not disappear into thin air:
Work remains to be done so that…
- Critical technical and organizational structures have already been hardened in advance in such a way that they no longer offer a relevant target for attack – which is probably more of a utopia,
- future technologies follow the security by design approach in such a way that their management becomes more manageable,
- Or the cyber security AI can be used at all levels and is also faster and better.
Implementation of cyber security
Above all, as is so often the case, is a management system that forms a framework for strategic and operational implementation measures, constantly questions itself and develops further. In addition to these “internal” processes of the management system, the findings of cyber security usually also have a very concrete effect on the following measures:
Building Expert and Rapid Response Forces:
It is not without reason that “digital first responders” and “BSI incident experts” are being trained and certified in a very up-to-date and highly effective manner, and rapid response teams for cyber security are being formed.
Cyber security must act as proactively as possible. Expert and rapid reaction teams as separate organizational units – or at least put together as virtual teams via “dotted lines” – are central tools here. Important for such teams is the right mix of…
- Experts from a wide variety of IT disciplines with in-depth technical know-how – in addition to infrastructure experts, experienced professionals from the field of critical application environments are the top priority here – such as SAP basis and security specialists,
- Experienced IT generalists with openness to unconventional ideas,
- nerds and hackers with technology faith and creativity,
- Already affected professionals with a touch of technical disillusionment,
- Social engineers for the human part of a system
Further technical and organizational measures:
Reacting in this cat-and-mouse game is far from enough to achieve the goal of cyber security as stably as possible. Different sub-areas have been established, which, in addition to their actual objectives, must also make an operational contribution to and in coordination with cyber security in advance:
- Network security: It is primarily responsible for protecting against internal and external attackers and malware with technical measures – network structures with hardware and software elements, technical and organizational security protocols: secure server and network configurations, defined IP segments, VPNs, firewalls, DMZ, … goal are hardened network components that together provide a risk-safe technical network
- Program security: It defines procedures and catalogs in order to release only such software for operation that poses as little security risk as possible. It includes technical tests of the software components and their interfaces, specifications for authorization concepts, minimum versions and updates, etc. The main focus is on infrastructure applications and business applications with great complexity, such as SAP systems with their entire transport routes across a wide variety of infrastructure and application nodes.
- Information security: It provides regulations for handling data: recording, storage, processing, and distribution. The GDPR, the ITSiG and, depending on the industry, different DIN/EN standards form the basis here.
- Disaster recovery and business continuity: if the attack could not be prevented and real damage has occurred, the processes of damage reduction and restoration of orderly business operations come into play. Depending on the nature and severity of the incident, this includes…
- Measures of a technical nature (e.g. server and data recoveries, restarting complex application environments),
- Measures of an organizational nature (running through emergency plans, but also operational provision of emergency jobs, also parallel to the restoration of operations also extended analysis and definition of further preventive measures) as well as
- Measures of a communicative nature (information of the specified state institutions and affected persons in the event of data leakage or other serious governance or DSGVO violations).
- Last but not least, user education and sensitization is a central part of the implementation of a cyber security strategy: a toe behind the limit of technically and organizationally sensible or feasible security concepts are people as the greatest and in some cases incalculable risk. Companies must never forget to include this in the form of information, transparency and training in the overall cyber security process.
The important role of external advice
Cybersecurity is a field that has to constantly prove itself on the test bench of the daily news. In this highly sensitive area, it has proven useful to make use of external support. Specialists like those from Firnkorn and Stortz advise companies on cyber security in the context of corporate architecture and with a view to processes, tools and interfaces: holistically and in the SAP environment in particular. As consultants and experts in cyber security, they provide comprehensive support and tailor-made advice according to the needs of your company in order to develop an optimal cyber security solution.
Also, read more on related topics
Your contact at Firnkorn & Stortz on the subject of cybersecurity

Firnkorn + Stortz GmbH
Thomas Firnkorn
