Information Security and IT Security
Relevance of information security
Why is information security important? Whether in business or in the public sector – organizations have never been more concerned with collecting, managing, using, interpreting and publishing information. And organizations have never been more willing to make purely fact-based decisions, to subordinate other decision-making criteria and values to the information base.
Information sovereignty means power. Information security ensures a stable and correct power base. Incorrect information, on the other hand – incorrectly collected, misinterpreted, maliciously foisted on or disseminated in public – can quickly lead to real or PR disasters for the organizations concerned.
Where information management wants to lay the foundation for good decisions, the discipline of information security should reduce wrong decisions due to incorrect or insufficient information. Because never before have the amount, timeliness and, above all, the correctness of available information had such an effect on serious strategic and operational action as it does today – leaving the special area “fake news” out of the picture.
Definition and core values of information security
Information security has a general definition: making the complete, correct information base available to your organization in a timely manner and keeping it free from false/incorrect information. In operational practice, however, there are often adapted implementations: In many organizations, information security is interpreted individually and charged with specific priorities. It is particularly often mixed up mentally with the actual sub-disciplines of IT security or cyber security or is completely equated with them.
First and foremost, however, information security is about ensuring the protection goals or protection classes of confidentiality, integrity and availability for ALL types of data and information (see below).
It describes both a status and the processes with which sensitive data is secured against unauthorized access and changes. For this purpose, the process model of information security defines organization-specific,
- the way in which existing or emerging threats are assessed both outside and within an organization
- how specific existing and future vulnerabilities are identified and protected, and
- how your own organization reacts to attacks – unsuccessful and successful.
Information security - a delimitation
In general, information security is an overarching term that summarizes a wide variety of (sub)disciplines – today primarily IT. These include IT security (in both forms IT safety and IT security), cyber security, IT governance.
In a narrower sense, information security differs in content from the above disciplines, but has many interfaces and overlaps with them, or one discipline intensively influences the other.
However, there are different focal points that justify separate consideration: While IT security and cybersecurity tend to focus on IT systems and networks, information security generally focuses on content – i.e. information – and how it is handled.
Sure, a large part of relevant information is now available in digital form. They are stored, transported, and processed. However, there are also many types of information that fall outside of the above disciplines:
Information that is exclusively or additionally available on classic storage media, in explicit form e.g. on all types of paper or e.g. blackboards and whiteboards, or implicitly in the heads of the employees, exchanged in direct conversations at meetings, in the coffee kitchen or with the partner at home. In addition to digitized data and information, all of these are also part of information security.
Irrespective of the nature of the information: if it leaks out unintentionally, is falsified or is suddenly no longer available and processable, this has at least annoying and often even critical effects for companies. For this reason, it is worthwhile for every company to give serious thought to information security. And that goes beyond the usual DIN, ISO and BSI specifications.
Ultimately, information security is roughly at the level of corporate governance and shares some concepts and goals with it, although the perspectives on them differ.
The primary goal of information security: reliability
The reliable availability of correct information for authorized persons: this is ultimately the central point of information security. This is also and above all a matter of the processes related to information: How and where is information created, how and where is it stored, processed, shared, deleted? How is it ensured that only desired and error-free changes take place, that they are within the framework of the law, and that the outflow of information is also avoided? On the other hand, information should be available correctly and as needed.
Protection goals of information security
To ensure reliability, derived protection goals of information security have primarily been established in three technical dimensions:
- Confidentiality: Data and information should only be accessible and changeable for people who have a legitimate interest in them to optimally carry out their internal company tasks. This reduces, for example, the risk of data leakage through personally known information.
- Integrity: data and information must be complete; data origin and data changes should be clearly marked.
- Availability: Data and information should be available in a timely and appropriate manner. In addition to general access options and suitable authorization concepts, this also includes disaster prevention with defined recovery times after physical (local or large-scale system failures) or logical incidents (faulty data changes or deletions). Likewise, when planning availability, the people who make the handling of this data possible in the first place must not be forgotten.
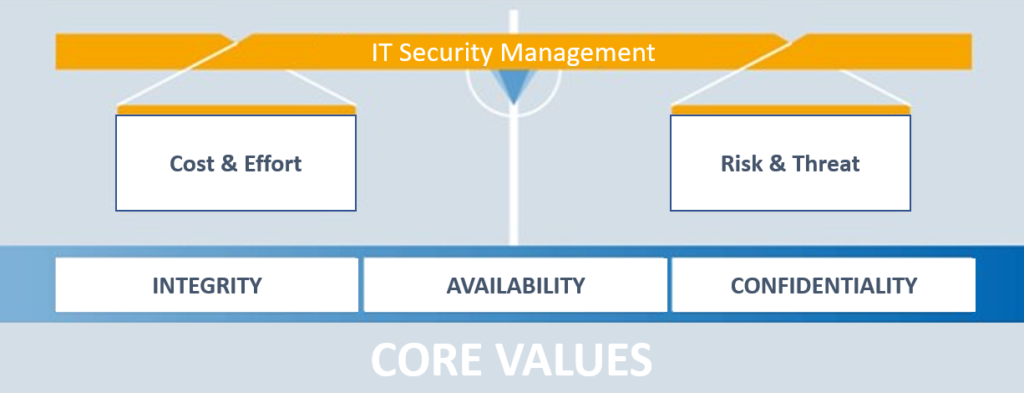
Figure 1: Basic values of information security
Source: https://www.shd-online.de/leistungsprofil/it-security/ or https://conjamo.de/beratung/it-security-und-informationssicherheit/
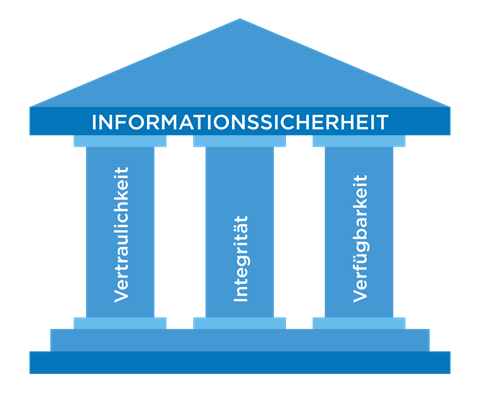
Figure 2: Pillars of information security
Source: https://www.fabasoft.com/de/news/blog/sicher-die-cloud-wie-das-geht
Especially in connection with the highly complex data structures and authorization concepts in SAP environments, which play a critical role in many commercial companies, these three dimensions are of central importance: in many companies, SAP systems are considered the leading systems for the sustainable storage, processing and distribution of data and information.
Structure of information security
Information security includes a whole complex of general structures and concrete measures, often referred to as information security management system (ISMS).
Irrespective of whether such a system is set up voluntarily or clearly prescribed according to the standards mentioned below or follows purely individual approaches, certain components should or must be present:
- Clearly named information security officers (ISB)
- Binding and transparent targets
- Clearly formulated guidelines
- Employee qualification for all employees according to their role
- Regular review and adjustment processes
- Continuous Improvement
- Specific measures for concrete incidents, but also general measures for previously unknown dangers.
Data Protection and Information Security
Information security requirements can be found primarily in risk management. In addition to company-specific objectives, they come from many national and international standards and laws.
The German IT-Grundschutz of the BSI and the Federal Data Protection Act have defined general criteria for information protection almost independently for a long time. With the German IT Security Act ITSiG, the KRITIS regulation and of course the European General Data Protection Regulation (GDPR) there has been a lot of movement and change in recent years – the latter in particular promises severe penalties as an additional motivation for non-compliance.
More specific approaches to information security can be found in the ISO/IEC 27000 series. International regulations such as the Sarbanes-Oxley Act (SOX) from 2002 also play an important role. And especially with regard to Industry 4.0, IEC 62443 is also gaining in importance, especially for industrial companies.
Implementation of Information Security
Measures
In addition to purely organizational measures to implement information security such as
- defined and above all documented processes for information management
- together with their permanent follow-up in day-to-day operations and public certification in the form of audits and certifications as well
- regular employee training to raise awareness of all those involved in handling data and information,
- Confidentiality: specific authorization management, physical (access control systems, etc.) and IT measures (user profiling in the IT infrastructure and in the applications)
- Integrity: (IT) governance structures, architecture management, IT development plans, etc. to support a functional interaction of all areas and components.
- Availability: Risk analysis, availability and disaster recovery measures covering all relevant risks.
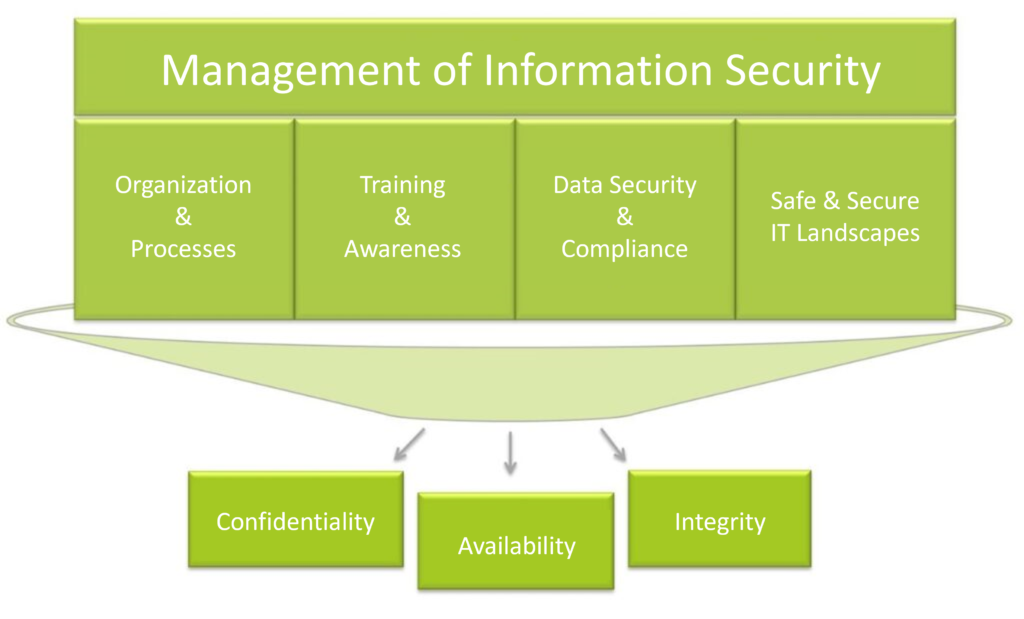
Abbildung 3: Management der Informationssicherheit
Quelle: https://www.it-daily.net/images/Bilder-ITS/Onlineartikel_ISO27001_2013_Bild1.jpg
Alone with a view to more or less complex SAP environments, a vast number of possibilities can be played through in the three protection goals mentioned above and implemented in almost any complexity: The SAP standard generally offers all the necessary software-technical possibilities. In terms of (not only) information security, there is a whole range of third-party solutions. From the point of view of existing skillsets and the daily operational effort, such extensions enable occasional, standard, and power users to make their work easier with a small one-off effort.
Information security and consulting in SMEs
In view of the increasing complexity and the ever-advancing technical progress, it makes sense for medium-sized companies to involve appropriately experienced external experts. They look at the risks and measures in a company-specific manner and under best-practice aspects. Otherwise, information security and related disciplines can quickly be brought into an unsuitable cost-benefit ratio.
In the past, the consultants from Firnkorn and Stortz have already shown, as competent consultants, which weak points open up in the environment of information security in a company. Concrete recommendations for action on how to deal with these gaps and the overall context of the company are also part of the advice and support for information security.
Also, read more on related topics
Your contact at Firnkorn & Stortz on the subject of information security

Firnkorn + Stortz GmbH
Thomas Firnkorn
